Reversing AWS IAM unique IDs
A few years ago, I wrote about determining AWS account IDs from AWS
access keys, i.e. those strings that begin with AKIA or ASIA. It's also
possible to determine information from other AWS IAM unique IDs, specifically
these two from the table in Amazon's docs.
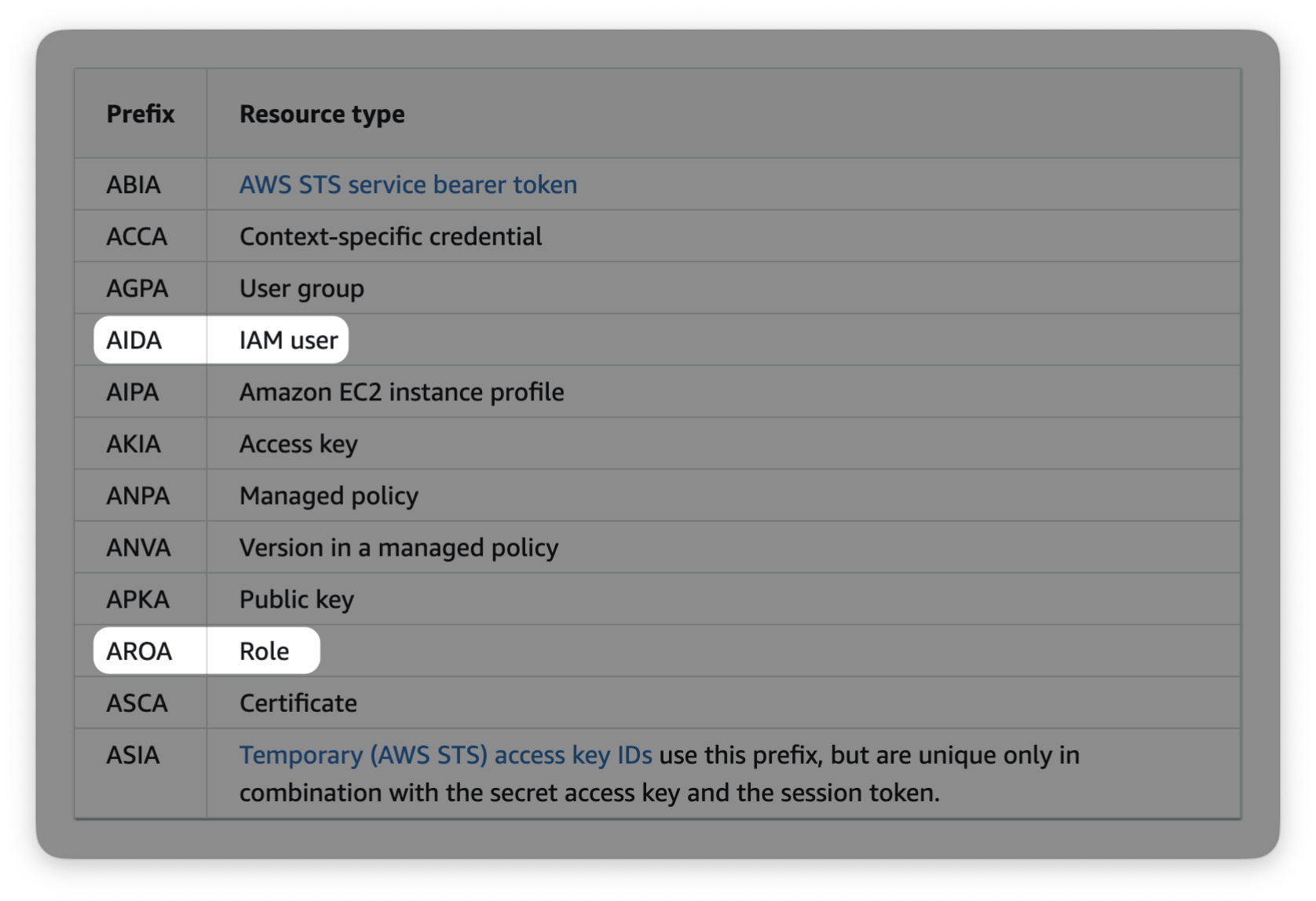
These unique IDs can pop up in a few places, but the place I see them most often is in CloudTrail logs when a principal in a different AWS account accesses a resource (like a KMS key or S3 bucket) in my account. In these situations, I often want to know the ARN of the user/role, because it's easier to understand my logs. As far as I know, the process for doing this is not documented and not well-known, so here's a blog post on how to do it:
- You have a unique ID. Let's say it's
AROAJMD24IEMKTX6BABJI(that's a real ID you can use to follow this blog post) - Create or find an unused S3 bucket that you control. Add the following to its bucket policy:
- Save the bucket policy.
- Now view the bucket policy. You'll see that AWS has automatically resolved the unique ID to the ARN of a role in my personal account:
There are a few things to know about this:
- Unique IDs only get resolved if they're in a
Principalpart of an AWS IAM policy statement. They won't get affected if they're elsewhere, e.g. aCondition. - It doesn't work for principals that have been deleted. If you try use a unique ID
of a deleted principal, you get an
Invalid principal in policyerror when you try to save the bucket policy. - If you save this bucket policy on day 1 and I delete the role in my account on day 2, then when you look at the bucket policy again on day 3 it will revert to showing you the original unique ID. This is how you know I've deleted the role. Even if I recreate a role with the same name, it won't reappear - because the new role gets a new unique ID (this is documented).